In the era of interconnected devices, securely connecting remote IoT systems is crucial for ensuring data privacy and system integrity. Whether you're a hobbyist or a professional, setting up a peer-to-peer (P2P) SSH connection on a Raspberry Pi can significantly enhance your network security without additional costs. This guide will walk you through the essential steps to achieve this efficiently.
As the Internet of Things (IoT) continues to expand, more devices are being integrated into our daily lives, creating new vulnerabilities. Securing these devices is not just an option—it's a necessity. By leveraging the power of SSH (Secure Shell), you can establish a robust connection between your remote IoT devices and a Raspberry Pi, ensuring secure communication.
This article will provide detailed instructions, tips, and best practices to help you set up a secure P2P SSH connection on your Raspberry Pi for free. You'll learn about the tools, configurations, and precautions necessary to protect your IoT ecosystem effectively.
Read also:Eniko Hart A Rising Star In The Entertainment Industry
Table of Contents
- Introduction to SSH
- Raspberry Pi Overview
- Why Secure Remote IoT Connections?
- Setting Up SSH on Raspberry Pi
- Establishing a P2P Connection
- Securing Your SSH Connection
- Troubleshooting Common Issues
- Best Practices for IoT Security
- Cost-Effective Solutions
- Conclusion
Introduction to SSH
SSH, or Secure Shell, is a cryptographic protocol designed to secure network communications. It provides a secure channel over an unsecured network, ensuring data integrity and confidentiality. By using SSH, you can remotely manage and control devices like your Raspberry Pi without exposing sensitive information.
Key Features of SSH:
- Encryption for data transfer
- Authentication mechanisms
- Secure file transfer capabilities
In the context of IoT, SSH is invaluable for maintaining secure communication between devices, especially when they are geographically dispersed.
Raspberry Pi Overview
The Raspberry Pi is a versatile, low-cost, single-board computer that has become a favorite among developers and hobbyists alike. Its compact size and powerful capabilities make it ideal for IoT projects. With its support for various operating systems and programming languages, the Raspberry Pi can be configured to act as a secure gateway for remote IoT devices.
Why Choose Raspberry Pi for IoT?
Raspberry Pi offers several advantages for IoT applications:
- Low power consumption
- Wide range of compatible hardware
- Extensive community support
These features make it an excellent choice for creating a secure IoT environment.
Read also:Santiago Gimeacutenez The Rising Star Of Mexican Football
Why Secure Remote IoT Connections?
Securing remote IoT connections is critical for protecting sensitive data and preventing unauthorized access. Without proper security measures, IoT devices can become vulnerable to cyberattacks, leading to data breaches and system failures.
Common Threats to IoT Security:
- Malware infections
- Man-in-the-middle attacks
- Unauthorized access
By implementing SSH and following best practices, you can mitigate these risks and ensure the safety of your IoT ecosystem.
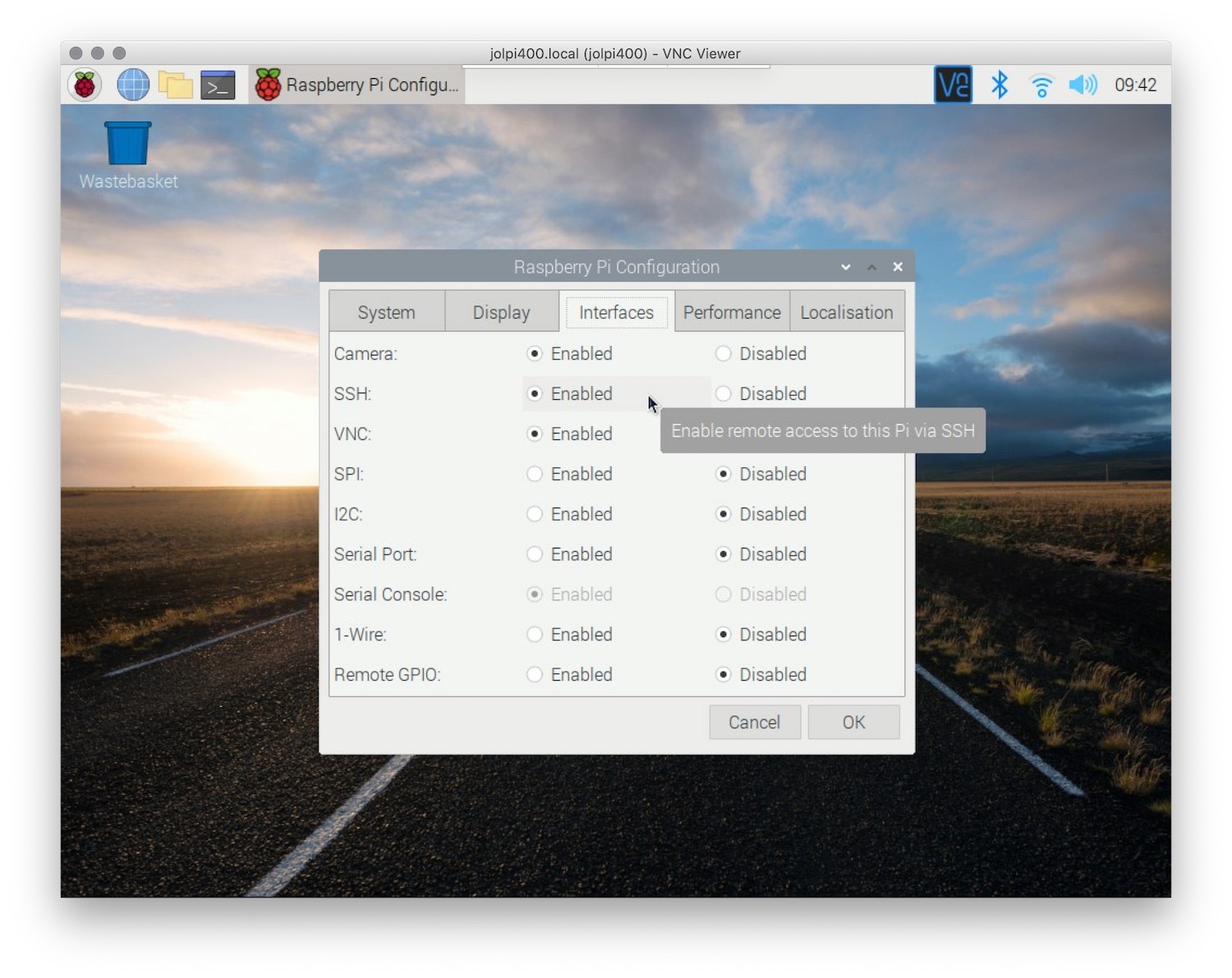
Setting Up SSH on Raspberry Pi
To securely connect your remote IoT devices, you first need to enable SSH on your Raspberry Pi. Here's a step-by-step guide:
Step 1: Enable SSH
On a Raspberry Pi running Raspbian, SSH is disabled by default. To enable it, follow these steps:
- Open the terminal on your Raspberry Pi.
- Type
sudo raspi-configand press Enter. - Navigate to "Interfacing Options" and select "SSH".
- Choose "Yes" to enable SSH.
- Reboot your Raspberry Pi.
Step 2: Configure SSH Keys
Using SSH keys instead of passwords enhances security. Here's how to set them up:
- Generate a key pair on your local machine using
ssh-keygen. - Copy the public key to your Raspberry Pi using
ssh-copy-id user@raspberrypi. - Test the connection by logging in with
ssh user@raspberrypi.
Establishing a P2P Connection
A P2P connection allows direct communication between devices without relying on a central server. To set up a P2P SSH connection:
Step 1: Identify Device IPs
Ensure you know the IP addresses of both devices. You can find the IP address of your Raspberry Pi by running ifconfig or ip addr in the terminal.
Step 2: Initiate the Connection
From your remote device, initiate the SSH connection using:
ssh user@raspberrypi_ip
This will establish a secure P2P connection between your devices.
Securing Your SSH Connection
While SSH provides a secure foundation, additional measures can further enhance your connection's security:
1. Disable Password Authentication
By disabling password authentication, you force users to use SSH keys, reducing the risk of brute-force attacks. To do this:
- Edit the SSH configuration file:
sudo nano /etc/ssh/sshd_config. - Set
PasswordAuthentication no. - Restart the SSH service:
sudo service ssh restart.
2. Use a Non-Standard Port
Changing the default SSH port (22) can deter automated attacks. Update the Port setting in the SSH configuration file and ensure your firewall rules are updated accordingly.
Troubleshooting Common Issues
Even with careful setup, issues may arise. Here are some common problems and their solutions:
1. Connection Refused
Possible Cause: SSH is not enabled or the firewall is blocking the connection.
Solution: Ensure SSH is enabled and check your firewall settings.
2. Permission Denied
Possible Cause: Incorrect SSH keys or permissions.
Solution: Verify the SSH keys and file permissions.
Best Practices for IoT Security
Adopting best practices is essential for maintaining a secure IoT environment:
- Regularly update your Raspberry Pi's software.
- Use strong, unique passwords for all accounts.
- Monitor network activity for suspicious behavior.
By following these guidelines, you can minimize security risks and protect your IoT devices.
Cost-Effective Solutions
One of the advantages of using a Raspberry Pi for IoT security is its cost-effectiveness. With minimal investment, you can create a secure, scalable IoT network. By leveraging free, open-source tools and software, you can further reduce costs while maintaining high security standards.
Conclusion
Securing remote IoT connections using P2P SSH on a Raspberry Pi is a practical and cost-effective solution for enhancing your IoT ecosystem's security. By following the steps outlined in this guide, you can establish a secure, reliable connection that protects your devices and data from potential threats.
We encourage you to share your experiences and insights in the comments below. Additionally, explore other articles on our site for more tips and tutorials on IoT security and Raspberry Pi projects. Together, let's build a safer, smarter connected world!